The new Ransomware unleashed on Tuesday, is more lethal on the systems it attacks -- and the financial motive is unclear
Bangalore, June 28 2017: The assault on computers worldwide which began in the Ukraine on June 27, appears on a superficial level, to be a replay of the scenario that prevailed at the so-called 'WannaCry' attacks six weeks ago. (See previous story).
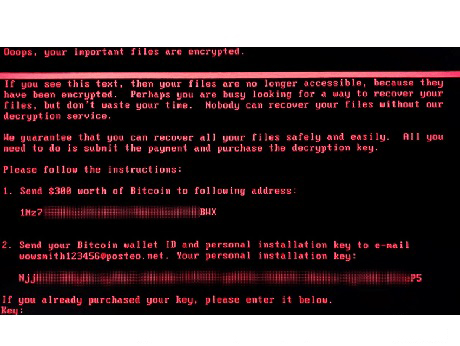
Once more corporates in a wide swath from the US to Russia to Scandinavia to Australia, and including India, have had their systems go down or access to their data blocked. In many -- but not all -- cases, this is accompanied by a demand to pay a ransom of the equivalent of $ 300 in bitcoins, to restore the deliver a key that restores computers to working order.
Last time around, in mid May, it hinged on vulnerabilities of Microsoft's Windows XP systems which had not applied the latest patch. This time the malware is more malicious: it attacks and encrypts the Master File Table ( MFT) of the hard drive and effectively destroys the Master Boot Record ( MBR) which means you cannot boot up the computer. The attackers are demanding that victims send their wallet numbers by e-mail to “wowsmith123456@posteo.net” and at the time of writing some 25 victims seem to have done so, remitting about $6000. This does not seem to be big enough money to make it worthwhile -- so analysts are suggesting the initial attacks -- mostly in the Ukraine where all ATMs in the capital Kiev, stopped working - may be a political attack against the Ukrainian government: It occurred a day before a holiday marking the adoption in 1996 of Ukraine’s first Constitution after its break from the Soviet Union.
But that does not explain why an assortment of global enterprises have also reported being affected -- Russia’s top oil producer Rosneft, Danish shipping giant A.P. Moller-Maersk, pharmaceutical company Merck & Co, German postal and logistics company Deutsche Post, French construction materials company and float glass maker Saint Gobain, Netherlands-based shipping company TNT and a unit of candy manufacturer Cadbury.
Computers at the India-based operations of German company Beiersdorf AG , the maker of Nivea skincare products and the Indian unit of British consumer goods company Reckitt Benckiser maker ofDettol and Lysol, have been reportedly attacked.
Ransom-as-a-service
Initially, the attack was said to be using the malware known as Petya ( which means Little Peter in Russian). Chillingly, Petya is available for sale on the so-called Dark Web. Anyone can buy it and get started down the path of demanding ransomware. This is being cynically dubbed "Ransom as a service" on the analogy of "Software as a Service". If so it will make detection that much more difficult since like a hydra-headed monster, multiple baddies could be cloning the initial attack.
However Kaspersky the Russia-based net security company, says this is not Petya and indeed, has dubbed in 'NotPetya' although it uses the same technology called EternalBlue, hacked from the US national security agency. It also warns that paying the ransom may be futile, since the perpetrators seem not to be interested in keeping their word.
So what to do? Presumably most enterprises keep a back up of data. The way to recover without succumbing to the cyber crooks is to disconnect the system from the Internet connection, reformat the hard disk and re load data from the back up, while ensuring the latest anti-virus and net security tools have been activated.