Bangalore, August 6 2015: The world woke up this week with the alarming news of the latest vulnerability of a piece of ubiquitous and widely used software -- Adobe's Flash.
The New York Times wrote: "For seven days, hackers used Yahoo’s ad network to send malicious bits of code to computers that visit Yahoo’s collection of heavily trafficked websites, the company said on Monday. The attack, which started on July 28, was the latest in a string that have exploited Internet advertising networks, which are designed to reach millions of people online. It also highlighted growing anxiety over a much-used graphics program called Adobe Flash......." ( full NYT story here)
David Emm, Senior Regional Researcher, UK with Kaspersky Lab’s Global Research and Analysis Team comments:
The latest news on cybercriminals abusing Yahoo’s ad network to infect computers, using vulnerabilities in Adobe’s Flash software highlight again how important it is to instantly patch systems when updates are available.
Cybercriminals tend to choose the path of least resistance, i.e. to focus on those things that provide an easy route to success – installing their malware on vulnerable computers. Flash Player is widely-used, providing a big pool of potential victims. It’s often left unpatched – people take its functionality for granted and tend to overlook it.
You will now again hear many recommendations that people should delete the plugin or turn it off. It is hard to give a general recommendation here, though. Many people are just used to flash and chose the ease of it over the security. But I would suggest that people ‘give it a go’, i.e. remove it and see what difference it makes to their browsing experience. If, after not having Flash Player for a while, they find out they don’t need it – leave it off the system completely. If not – simply re-install it.
Brian Krebs recently shared his experience of living without Flash Player here. In between the two positions – i.e. on or off – people can modify their browser settings to allow Flash on-demand, allowing it only when accessing trusted websites. But the Yahoo-case shows that it is a very difficult task to determine which websites can be trusted or not. I assume most people would trust Yahoo.
I believe Flash will stay on computers for a while, just because it is such a widely used technology. Like Java, it’s installed on many computers by default and people tend not to think about it until there’s a well-publicised problem. While some popular websites are already replacing Flash with the HTML5 technology (e.g. Youtube), some others still rely on Flash, forcing users to enable/install Flash Player in their browsers to be able to see the content. Nevertheless, the security issues are constantly pushing the shift in web technologies, even if the full transition may take some time.
MEANWHILE... Kaspersky Lab’s Security Bulletin 2014 which quantifies Web vulnerabilities finds:
In 2014, there were 1,432,660,467 attacks launched from online resources located all over the world. The main attack method – via exploit packs – gives attackers an almost guaranteed opportunity to infect the user computer if it is not protected with a security solution and if it has at least one popular and vulnerable (not updated) application installed.
Vulnerabilities:
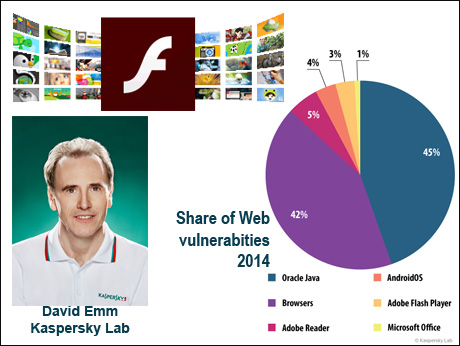
In 2014, the fraudsters most often exploited Oracle Java vulnerabilities. However, the popularity of Java vulnerabilities declined steadily throughout the year, and its overall share was less than half of last year’s figure – 45% against 90.5% 12 months ago. This might be due to the closure of old vulnerabilities and a lack of information about any new ones.
Second place was occupied by the Browsers category (42%) which includes exploits for Internet Explorer, Google Chrome, Mozilla Firefox, etc. According to the quarterly ratings, for much of 2014 this was the leading category but it didn’t quite outstrip the large number of Java exploits in late 2013 and early 2014.
Adobe Reader exploits were in third place (5%). These vulnerabilities are exploited in drive-by attacks via the Internet, and PDF exploits form part of many exploit packs.During the year, we saw a decrease in the number of attacks using exploit packs.
As we can see, (pie chart in our illustration) Flash figures rather low in the vulnerability ranking -- but because it is so widely used, Indian users need to be aware of the dangers -- and the limited remedies they can deploy.