Malware designed to bypass traditional Net security systems, capture key strokes, hard disk contents, video and audio files -- every 10 seconds.
Mail to ambassador spoofed a letter from Defence Minister Parikkar, say analysts of US-based cybersecurity company, Palo Alto Networks.
Bangalore, March 7 2016: The Indian embassy in Kabul, Afghanistan -- specifically the ambassador -- has been the target of a cyber attack, which was aimed at snooping on sensitive documents, mail, audio recordings, still pictures and video footage.
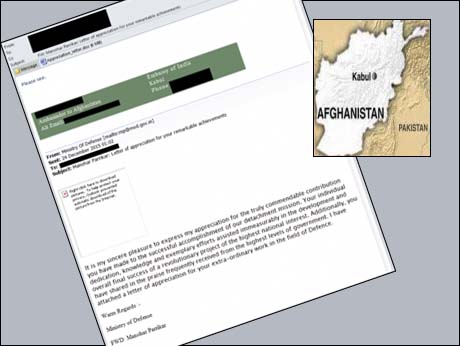
The Threat Intelligence team of the US-headquartered cyber security solutions company, Palo Alto Networks which monitors cyber traffic and potential attacks world-wide has reported that on Christmas eve last year, the Kabul embassy was the object of a targeted attack in the form of an e-mail addressed personally to the ambassador ( at the time, Amar Sinha). The mail was in fact a spoof, cleverly crafted to look like a communication from Defence Minister, Manohar Parikkar, congratulating the ambassador for his ' commendable contribution' and lauding his 'individual dedication , knowledge and exemplary efforts' for a ' project of the highest national interest'.
In a telephone briefing for IndiaTechOnline from Singapore, Vicky Ray, Senior Researcher with "Unit 42", the Palo Alto Networks Threat Intelligence team, who with fellow analyst, Tokyo-based Kaoru Hayashi, first tracked and identified the malware, explained that the spoof e-mail was an instance of Spear Phishing -- malware specifically designed to attack one victim, by posing as an email from a known and hence trusted source.
The mail to the ambassador, had a 6 MB Word attachment entitled " Appreciation_letter.doc" . If the recipient opened this attachment, in a vulnerable version of Word, it would have breached the recipient computer's security and installed a downloader software in it -- what is called a 'Trojan' , which is what its name says -- a Trojan Horse with malicious software hidden inside.
Many antivirus programmes might just not detect the malware, Ray says, because it avoided sending out the "signature" that net security tools used to recognize malicious content. Like a terrorist disassembling a weapon and transporting it in pieces to avoid detection, the unknown authors, sent the malware in innocuous chunks.
Once inside the computer, the Trojan downloader was designed to download an "exe" or executable file with multiple plug-ins, many of them using standard Open Source tools. But they were diabolically designed: Each innocent-looking plug-in had a specific task: one to search for files on any attached USB device or any removable drives; another to log key strokes, a third to steal files on the hard disk. This last plug-in was designed to search for specific types of files -- PDFs, Word documents, Powerpoint presentations, Excel spreadsheets -- and copy them every 60 minutes.
Another thread of the malware. executed backdoor commands -- snapping photos using the computer's own web cam, recording audio from audio port, taking screen grabs....
Ray and Hayashi found that nameless cyber baddies targeting the Kabul embassy , used tools like OpenCV , that a lot of legitimate organizations harness to capture and process images in security systems, driver-less cars -- and the Mars Rover project -- then misused the same code for their spying. In a back handed complement, the two analysts have dubbed the Kabul malware "Rover". Though they could track it to the minutest detail, they have no knowledge or proof that it actually breached the security of the embassy computer. Nor could they identify the country from where the cyber attack was launched.
Based on their monitoring studies they have created a "Rover Tag" to help customers of Palo Alto Networks' cyber security solutions, identify and neutralize this specific threat. They have documented the detection and analysis of this threat in a Blog earlier this week which can be found here ( revised 0830 IST 7 Mar 2016)