Bangalore, January 28 2016: US-headquartered security solutions compamny Palo Alto Networks, has been tracking a series of cyberattacks by a single hacker group, codenamed Scarlet Mimic, which seem to be targeting activists of minority groups in Tibet, Russia and India.
The attacks have primarily targeted against Tibetan and Uyghur activists as well as those who are interested in their causes. Similar attacks have also been identified against government organizations, who are responsible for tracking activist and terrorist activities, in Russia and India.
Palo Alto studies suggest Scarlet Mimic has also started to expand its espionage efforts from PCs to mobile devices, making an evolution in its tactics. The company hopes hopes to expose the tools, tactics and infrastructure deployed by Scarlet Mimic, in order to increase awareness of the threat and decrease its operational success through deployment of prevent and detection countermeasures.
The attacks began over four years ago and their targeting pattern suggests that this adversary’s primary mission is to gather information about minority rights activists. Palo Alto sayas: We do not have evidence directly linking these attacks to a government source, but the information derived from these activities supports an assessment that a group or groups with motivations similar to the stated position of the Chinese Government in relation to these targets is involved. Individuals and groups of all different types may become the target of cyber espionage campaigns. The most well known victims of cyber espionage are typically government organizations or high-tech companies, but it’s important to recognize that espionage-focused adversaries are tasked to collect information from many sources.
The Scarlet Mimic attacks primarily centre around the use of a Windows backdoor named “FakeM.” It was first described by Trend Micro in 2013 and was named FakeM because its primary command and control traffic mimicked Windows Messenger and Yahoo! Messenger network traffic to evade detection. We have identified two subsequent variants of the FakeM family, which has undergone significant changes since it was exposed in 2013. Palo Alto o identified nine distinct “loader” malware families, which Scarlet Mimic appears to use to avoid detection when infecting a system.
In addition to the FakeM variants, Scarlet Mimic has deployed Trojans that target the Mac OS X and Android operating systems.
To infect individuals with access to the data the actors desire, Scarlet Mimic deploys both spear-phishing and watering hole (strategic web compromise) attacks.
____________________________________________________
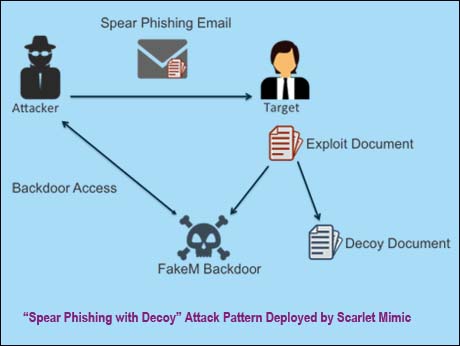
How spear phishing attack works ( see illustration above)
The attacker sends a spear-phishing e-mail with a subject and
body content that appeal to the targeted user. This e-mail carries
an attachment, which is typically a document that exploits a
Microsoft Office vulnerability. The attachment uses a file name
that is related to the e-mail content to trick the user into opening it.
|If the user opens the file and the exploitation is successful, a
backdoor Trojan is installed on the system that gives the attacker
access and a decoy document is displayed to the victim.
Decoy documents are typically non-malicious versions of the
content the user expected to see when opening the attachment.
______________________________________________________
For more information, please see blogpost here.