Bangalore, May 9 2013 – India has seen a 280 percent increase in bot infections that is continuing to spread to a larger number of emerging cities in India. Unsurprisingly therefore, the country accounts for nearly 15 percent of global bot-net spam, responsible for disseminating an estimated 280 million spam messages per day worldwide. These are findings in Symantec Corp.’s Internet Security Threat Report, Volume 18 (ISTR) released last week. The report highlights a 42 percent surge during 2012 in global targeted attacks, as compared to the prior year. Designed to steal intellectual property, these targeted cyber espionage attacks are increasingly hitting small businesses, which are the target of 31 percent of these attacks across the world.
Said Anand Naik, Managing Director-Sales, India & SAARC, Symantec, during a telebriefing for Indian media: “This year’s ISTR shows a clear focus among cybercriminals at targeting individuals, systems and organizations where the highest profits can be made. India continues to rank high in the list for even the most basic threats, pointing to an urgent need for improved awareness levels and security measures, even as the country’s adoption of Internet and mobile technologies is on the rise.”
Key Highlights
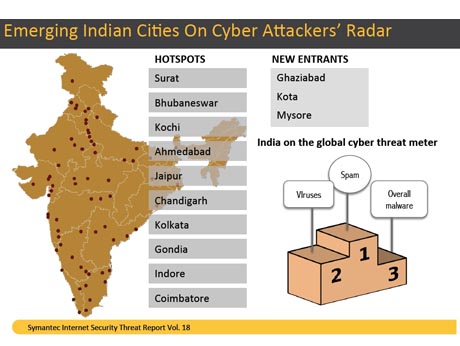
Emerging Indian Cities Remain on Cyber Attackers’ Radar The Indian security threat landscape witnessed a 280 percent increase in bot infections. While cities including Bhubaneswar, Surat, Cochin, Jaipur, Vishakhapatnam and Indore continue to see bot infections, some of the new entrants inducted to the list of bot infected locations in 2012 are Kota, Ghaziabad and Mysore. Bot infected computer activities can be classified as actively attacking bots or bots that send out spam such as spam zombies. Spam zombies are remotely controlled, compromised systems specifically designed to send out large volumes of junk or unsolicited email messages. The email messages can be used to deliver malicious code and phishing attempts. Globally, India is ranked first for spam zombies with 17 percent of spam zombies located in the country. Evidently the country is responsible for disseminating into cyberspace an estimated 280 million spam messages per day.
Small Businesses Are the Path of Least Resistance Targeted attacks are growing rapidly among businesses with fewer than 250 employees. Globally, small businesses are now the target of 31 percent of all attacks, a threefold increase from 2011. Attackers hone in on small businesses that may often lack adequate security practices and infrastructure. An indicator of this trend extending to India is that small businesses received the highest number of phishing and virus-bearing emails. One in 661 emails was a phishing email for small Indian businesses and one in 248 emails carried a virus, while for larger Indian enterprises with 1,000-1,500 employees, one in 4,751 emails was a phishing email and one in 1,611 carried a virus.
Additionally, small businesses and organizations can become pawns in more sophisticated attacks. Driven by attack toolkits, in 2012 the number of global web-based attacks increased by one third and many of these attacks originated from the compromised websites of small businesses.
Increase in Cyber Espionage - Knowledge Workers Face Targeted Attacks. The global average number of targeted attacks per day in 2012 was 116, compared with 82 in 2011 and 77 in 2010, recording a 42 percent increase in targeted attacks. Targeted attacks such as Disttrack in 2012 are commonly used for the purposes of industrial espionage to gain access to the confidential information or intellectual property on a compromised computer system or network.
Worldwide, the targets for attack in 2012 were knowledge workers who create the intellectual property that attackers want (27 percent of all targets in 2012) and those in sales (24 percent in 2012). The presence of a large number of knowledge workers makes India, a potential target for attackers, with IT services featuring in the top list of industries targeted for spam, phishing and viruses. In fact, India was home to 16 percent of viruses and globally, it ranked second for virus prevalence, just behind the United States. India also ranked third for overall malicious code.
Mobile Malware Put Consumers and Businesses at Risk Symantec’s recent mobility surveys reveal that 68 percent Indians are addicted to their mobile devices and 72 percent of Indian businesses faced mobility incidents due to malware infections, spam incidents, exposures of information, breach of information due to lost/stolen devices and phishing/social engineering instances. The focus on exploiting mobile devices will only grow with the increasing dependence on mobile devices for everything from simple email to critical apps and even mobile payments. In fact, Symantec predicts that 2013 will be a watershed year for mobile malware.
Last year, mobile malware increased by 58 percent, and 50 percent of mobile malware created in 2012 attempted to steal information or track movements. Symantec believes that whether cybercriminals are attacking computers, mobile phones or social networks, their ultimate goal is to obtain personal information including banking details, phone numbers and email addresses of friends and business associates, and even steal the target’s identity.
Additional resources
1. 2013 Internet Security Threat Report 2. Making sense of the numbers in Internet Security Threat Report Volume 18
Tech Notes: We alert you to some new buzzword in the Net security business:
SPEAR PHISHING: sending an email to a person of interest
... an e-mail spoofing fraud attempt that targets a specific organization, seeking unauthorized access to confidential data
WATERING HOLE ATTACK: Infect a website and lie in wait .. as a lion would do... an alternative to Spear Phishing. In a “Watering Hole” attack, the attacker compromises a site likely to be visited by a particular target group, rather than attacking the target group directly.